Introduction
Modern software applications often rely on a combination of proprietary code, open-source libraries, and third-party components.
Ensuring legal compliance, security, and streamlined management is fundamental for engineering leaders and Chief Technology Officers (CTOs).
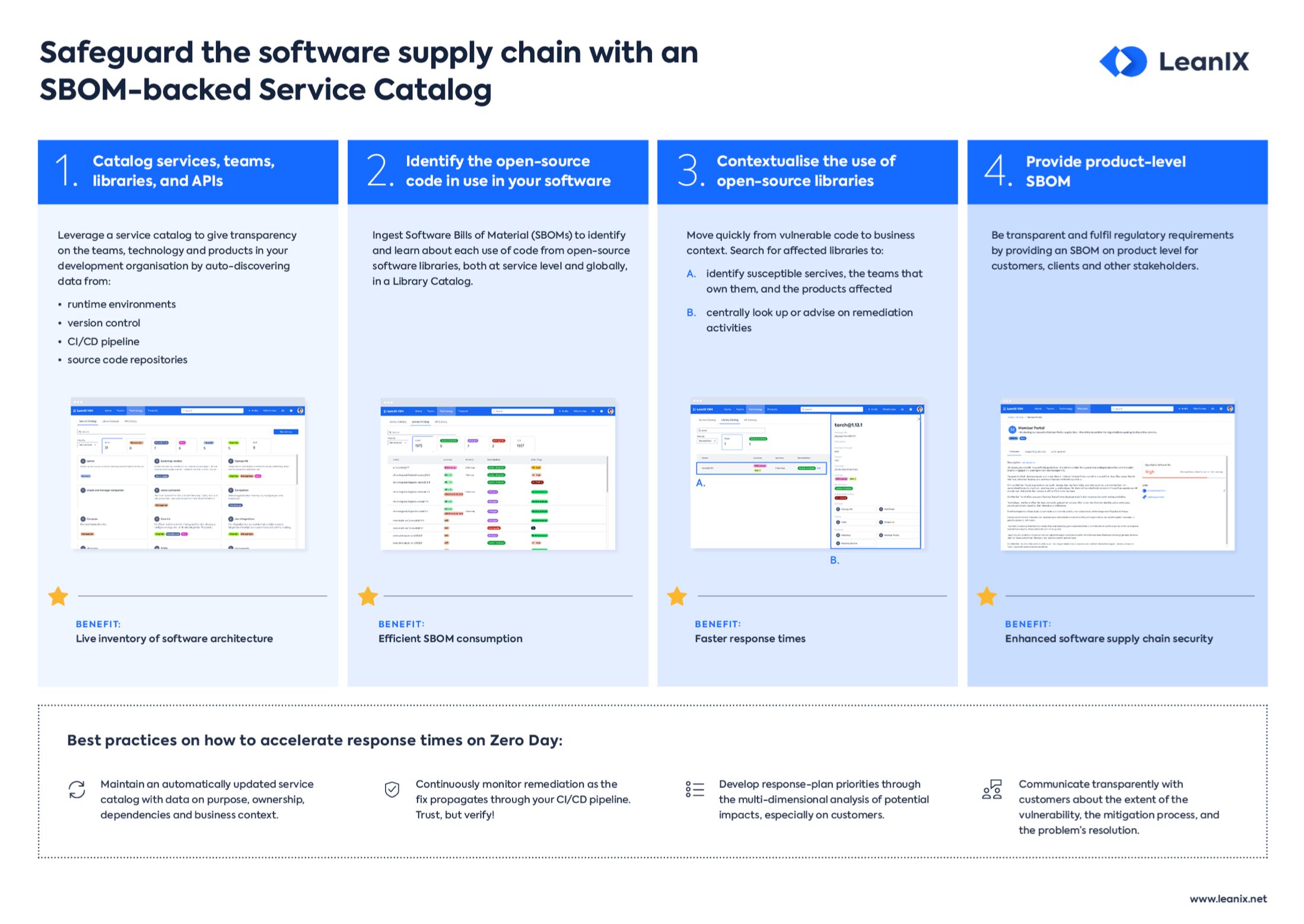
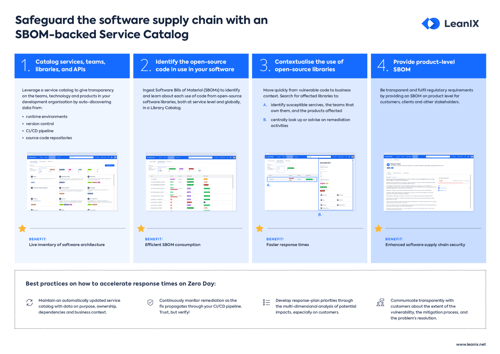
To address these challenges, organizations rely on a Software Bill of Materials (SBOM) – a comprehensive inventory of all components within their software.
That's where our Software Bill of Materials Hub comes in. This Hub is a definitive guide including a curated collection of articles, whitepapers, and other resources that provide a wealth of information.
Whether you're just getting started with SBOMs or you're a seasoned pro, you'll find valuable insights and practical advice that can ensure a fluid SBOM initiative.
What is a Software Bill of Materials (SBOM)?
A Software Bill of Materials (SBOM) is a detailed record of all components within a software application, including open-source libraries, third-party dependencies, licenses, and known vulnerabilities.
It plays a crucial role in managing dependencies, ensuring legal compliance, mitigating security risks, and providing transparency within an organization.
While software metadata provides broader information about the software itself, SBOM focuses on the components and dependencies used in a software application.
SBOM can be seen as a subset of software metadata, specifically focusing on the inventory and composition aspects of the software.
If you want to explain SBOM to a child, try this: "SBOM, or "Software Bill of Materials", is like a detailed list of all the ingredients used to make a pizza. This includes not just the main ingredients, like dough or cheese, but also all the toppings and even the type of oven used for baking. The SBOM tells you everything that goes into making the software (or pizza), where it comes from, and how it all fits together. This is very important for understanding what's in the software, especially if something goes wrong, like if there's a bad topping on the pizza or a problem with the code. It also helps people make sure that the software is safe and good, just like how a list of ingredients can help you check if the food is healthy and allergen-free.”
History
The history of the Software Bill of Materials (SBOM) can be traced back to the growing complexity and interconnectedness of software systems. As software development evolved, developers started relying on various components and libraries to expedite the process.
However, this brought challenges such as security vulnerabilities and license compliance issues. The concept of SBOM emerged as a solution to address these challenges. It draws inspiration from the manufacturing industry's Bill of Materials, which documents the components used in a product.
The idea of applying this concept to software gained prominence with the increasing use of open-source software.
In recent years, high-profile cyberattacks and supply chain breaches highlighted the need for improved transparency and security in software supply chains. Regulatory bodies, industry organizations, and cybersecurity experts recognized the importance of SBOMs for enhancing software security and managing supply chain risks.
In 2021, the United States National Telecommunications and Information Administration (NTIA) released a formal definition of SBOM, promoting its adoption as a best practice.
Additionally, several industry initiatives and standards organizations, such as OWASP and SPDX, have contributed to the development and promotion of SBOM standards and tools.
📚 Related: SBOM Time Act, SBOM EO 14028, and SBOM CISA Regulation





/EN/Tools/EA-Maturity-Thumbnail.png?width=260&height=171&name=EA-Maturity-Thumbnail.png)