Introduction
Open-source software has become an integral part of modern software development due to its accessibility, cost-effectiveness, and flexibility.
However, the use of open-source components also comes with a unique set of security challenges, including the risk of open-source vulnerabilities.
These vulnerabilities are weaknesses in open-source code that can be exploited by malicious entities to compromise systems and steal sensitive information.
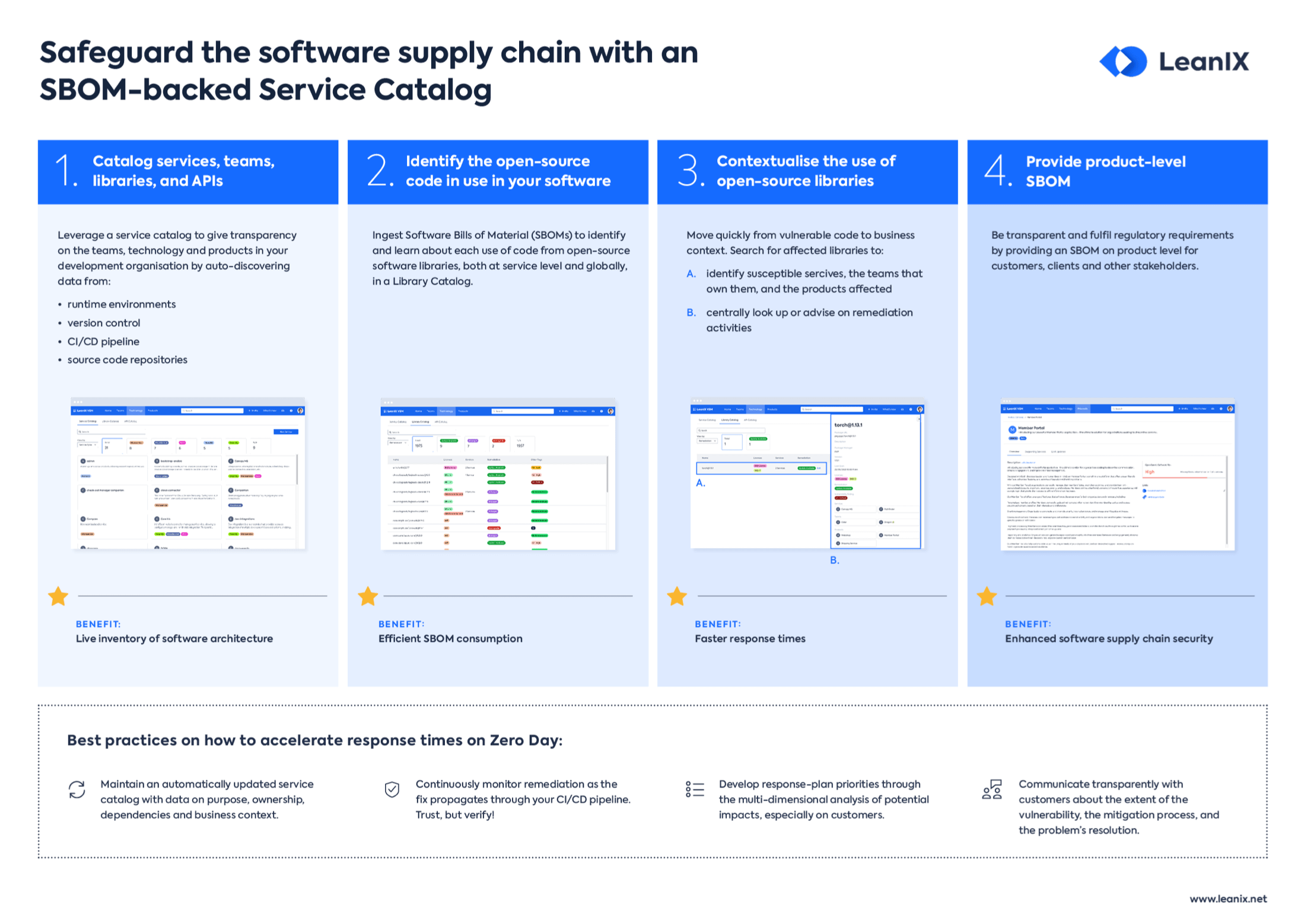
Managing these vulnerabilities effectively requires comprehensive approaches, including the use of a Software Bill of Materials (SBOM), which is an essential part of understanding and mitigating the risks in the software supply chain.
📚 Related: Open-Source License Types
What is an open-source vulnerability?
An open-source vulnerability is a flaw or weakness within the codebase of open-source software that can be exploited to compromise the security of the software or the system it operates within.
Due to the transparent and collaborative nature of open-source development, the code is accessible to all, including potential attackers. While this open nature facilitates collective knowledge and rapid improvement, it also exposes potential vulnerabilities that can be found and exploited.
A vulnerability might exist because of oversights or errors made during the software development process. It could be as simple as a piece of code that fails to validate user input correctly, or as complex as a subtle design flaw that undermines the software's overall security architecture.
In some cases, these vulnerabilities are found and reported by the open-source community members who are reviewing the code.
However, there are also instances where malicious actors discover these vulnerabilities and exploit them for nefarious purposes before they are identified and patched by the community.
📚 Related: Open-Source Vulnerability Database
Vulnerabilities and SBOM
A Software Bill of Materials (SBOM) provides a list of components in a software product.
It's crucial for vulnerability mitigation as it provides visibility into the software inventory, helping identify which components may be affected by newly discovered vulnerabilities.
This is why, SBOMs became an integral part of modern software development and security practices.
📚 Related: Software Dependencies
[READ ON BELOW]
/EN-Mitigate_Security_Vulnerabilities_like_Log4shell_with_a_Service_Catalog-Thumbnail.png?width=360&height=255&name=EN-Mitigate_Security_Vulnerabilities_like_Log4shell_with_a_Service_Catalog-Thumbnail.png)





/EN/Tools/EA-Maturity-Thumbnail.png?width=260&height=171&name=EA-Maturity-Thumbnail.png)