What is technology risk assessment?
Technology risk assessment is a systematic process to identify, analyze, and manage risks associated with the use and governance of technology within an organization.
Under the umbrella of technology risk management and technology lifecycle management, it works to protect against problems that could interrupt operations, expose data, or lead to financial loss.
📚 Related: Obsolescence Risk Management Solution
Technology risk assessment vs. IT risk assessment vs. information security risk assessment
While the terms technology risk assessment, IT risk assessment, and information security risk assessment are often used interchangeably, they focus on different aspects of an organization's technology and risk landscape.
Technology risk assessment focuses broadly on the risks associated with using, managing, operating, and adopting technology within an organization. It covers many risks like cyber threats, system failures, data problems, and following compliance with technology standards. The goal is to identify and mitigate risks that could impact technology's ability to support business objectives effectively.
IT risk assessment is a subset of technology risk assessment, primarily concentrating on the information technology infrastructure of an organization. It involves evaluating risks related to IT systems, networks, and data management processes. The assessment aims to ensure the reliability, availability, and security of IT resources, addressing risks from both technical and operational perspectives.
Information security risk assessment delves into risks specifically related to data confidentiality, integrity, and availability. It identifies vulnerabilities and threats to an organization’s information assets, including risks of unauthorized access, data breaches, and loss of sensitive information. This assessment develops strategies to protect data against cyber threats and ensure compliance with data protection laws and regulations.
📚 Related: The What Behind the Technology Obsolescence Management
Why are technology risk assessments needed?
In an era of rapid technological evolution, organizations face increasing threats from cyber attacks, data breaches, and technology obsolescence.
Proactive risk assessment enables you to make informed decisions about mitigating potential threats to your operations and strategic goals.
📚 Related: The Why Behind the Technology Obsolescence Management
Main use cases
- Managing technology obsolescence: Identifying technologies at risk of becoming obsolete and planning upgrades or replacements.
- Compliance with technology standards: Ensuring IT systems and processes comply with relevant industry standards and regulations.
- Cybersecurity threats: Evaluating vulnerabilities to cyber attacks and implementing appropriate security measures.
When is technology risk assessment needed?
The frequency of technology risk assessments can vary based on several factors, including the organization's industry, the pace of technological change, and the regulatory environment.
It is not a one-time activity but an ongoing process that should be integrated into the organization's broader risk management strategy and performed at least once a year.
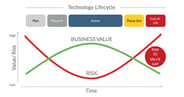
Image: Technology Lifecycle vs. Value & Risk
Here are key instances when technology risk assessments are particularly needed:
- During strategic planning: Assessments should be conducted as part of the strategic planning process to ensure that new technologies align with business objectives and do not introduce unacceptable risks.
- Before implementing new technologies: Before the adoption or deployment of new IT systems, software, or hardware to identify potential security vulnerabilities, compatibility issues, or impacts on existing systems.
- Following significant technological changes: Any major update or overhaul of IT infrastructure warrants a risk assessment to manage the transition effectively and mitigate potential disruptions.
- In response to emerging threats: As new cybersecurity threats emerge, regular risk assessments help organizations stay ahead of potential vulnerabilities.
- Regulatory compliance checks: To ensure ongoing compliance with evolving industry regulations and standards, particularly those related to data protection and cybersecurity.
- After security breaches or incidents: Conducting a post-incident risk assessment can identify vulnerabilities that were exploited and prevent future incidents.
- After an asset's End-of-Life – EoL stage: Assessment is needed when an asset expires out of the End-of-Life stage. Especially if the asset was critical to the business or had many dependencies.
How to perform a technology risk assessment?
Performing a technology risk assessment involves a series of structured steps to identify, analyze, and manage risks associated with technology within an organization.
Here’s a high-level overview step-by-step guide:
- Identify assets and IT components: Begin by cataloging all IT assets, including software, hardware, components, and data. For each system, connect infrastructure and application architectures with your CMDB provider and make sure to enrich your IT components lifecycle catalog. Utilize tools like enterprise architecture platforms to gain a comprehensive view of the IT landscape and its vulnerabilities.
- Assign criticality: For each IT asset, determine its business criticality, functional fit, technical fit, and the potential impacts of leakage, alteration, deletion, or unavailability. Additionally, classify the information category of data handled by each asset. Understanding these aspects is crucial for prioritizing risk management efforts based on the asset's importance to the organization.
- Identify dependencies: Map out the dependencies between IT assets, identifying which assets rely on others (children) and which assets are dependent upon (parents). This step helps in understanding the potential cascading effects of risks and planning mitigation strategies accordingly.
- Define business information: Assign relevant users, business capabilities, business processes, and lifecycle information to each IT asset. This information links the technical aspects of IT assets with their business context, highlighting the potential operational impact of technology risks.
- Identify risks: With a clear understanding of assets, their criticality, dependencies, and business context, proceed to identify specific risks to these assets. Identify:
- Assets running on outdated technology, including those nearing end-of-life (EoL) or end-of-support (EoS)
- Redundant or ill-fitted assets
- Critical assets with a low technical or functional fit
- Critical assets with complex dependencies
- Assess risks: Evaluate the risk’s likelihood and potential impact on the organization. This assessment can be qualitative, quantitative, or a combination of both. Factors to consider include the sensitivity of the data involved, the criticality of IT systems to business operations, and the potential financial and reputational costs of a risk event.
- Accept the risk: In some cases, the cost of addressing a risk may outweigh the benefits. Decision-makers can use LeanIX reports to understand the implications fully and may choose to accept the risk with full knowledge of its potential impact.
- Address the risk: For risks deemed unacceptable, use EA tools, such as LeanIX to support the initiation of action plans. This might involve rationalization, modernization, or other mitigation strategies.
- Mitigate risks: Develop application roadmaps to mitigate identified risks. This could involve implementing new security measures, updating or replacing EoL and EoS (outdated) systems, enhancing data encryption, or developing contingency plans for IT system failures. Prioritize actions based on the severity and likelihood of risks. Test new technology before migrating the whole organization or department.
- Use data-driven prioritization: With a wealth of data points you collected in early steps, you can make informed decisions, based on the lifecycle state of IT components, availability of successors, the business context of affected applications, time horizon for action, and associated costs. Prioritize based on a holistic view of the risk landscape, ensuring resources are allocated effectively to areas of the highest impact.
- Monitor risks: Establish ongoing monitoring of the IT environment to detect new or evolving risks. This includes regular security scans, compliance checks, and performance monitoring of IT systems.
- Create reports: Compile the findings from the risk identification, assessment, and mitigation steps into a comprehensive report. The reports serve as a crucial document for informing senior management, guiding decision-making, and documenting compliance efforts.
📚 Related: The Who Behind the Technology Obsolescence Management
Key components of a risk assessment report
- Executive summary: Overview of the assessment’s scope, key findings, and recommendations.
- Methodology: Explanation of the methods used to identify and assess risks.
- Risk details: Comprehensive listing of identified risks, including their sources, likelihood, potential impact, and current controls.
- Mitigation actions: Description of proposed or implemented actions to manage identified risks.
- Monitoring and review plan: Outline the ongoing risk monitoring strategy and schedule for future risk assessments.




/EN-Tech-Stacks-Poster_Resource_Page_Thumbnail.png?width=260&height=171&name=EN-Tech-Stacks-Poster_Resource_Page_Thumbnail.png)