Introduction
Performing a Software-as-a-Service (SaaS) security assessment is a vital part of any company's quality assessment protocol when evaluating potential vendors. Data stored through SaaS is not stored on-premise, which means sensitive and confidential data becomes more at risk from security breaches from the outside. It is important that all new SaaS in your portfolio meets the regulatory standards of your company.
A SaaS security questionnaire will ask where the data will be stored, what security measures are in place to ensure data safety, and make sure the vendor is up-to-date with data protection rules and certificates – along with various other questions.
Following general SaaS security best practices and a well-defined checklist will guide this assessment.
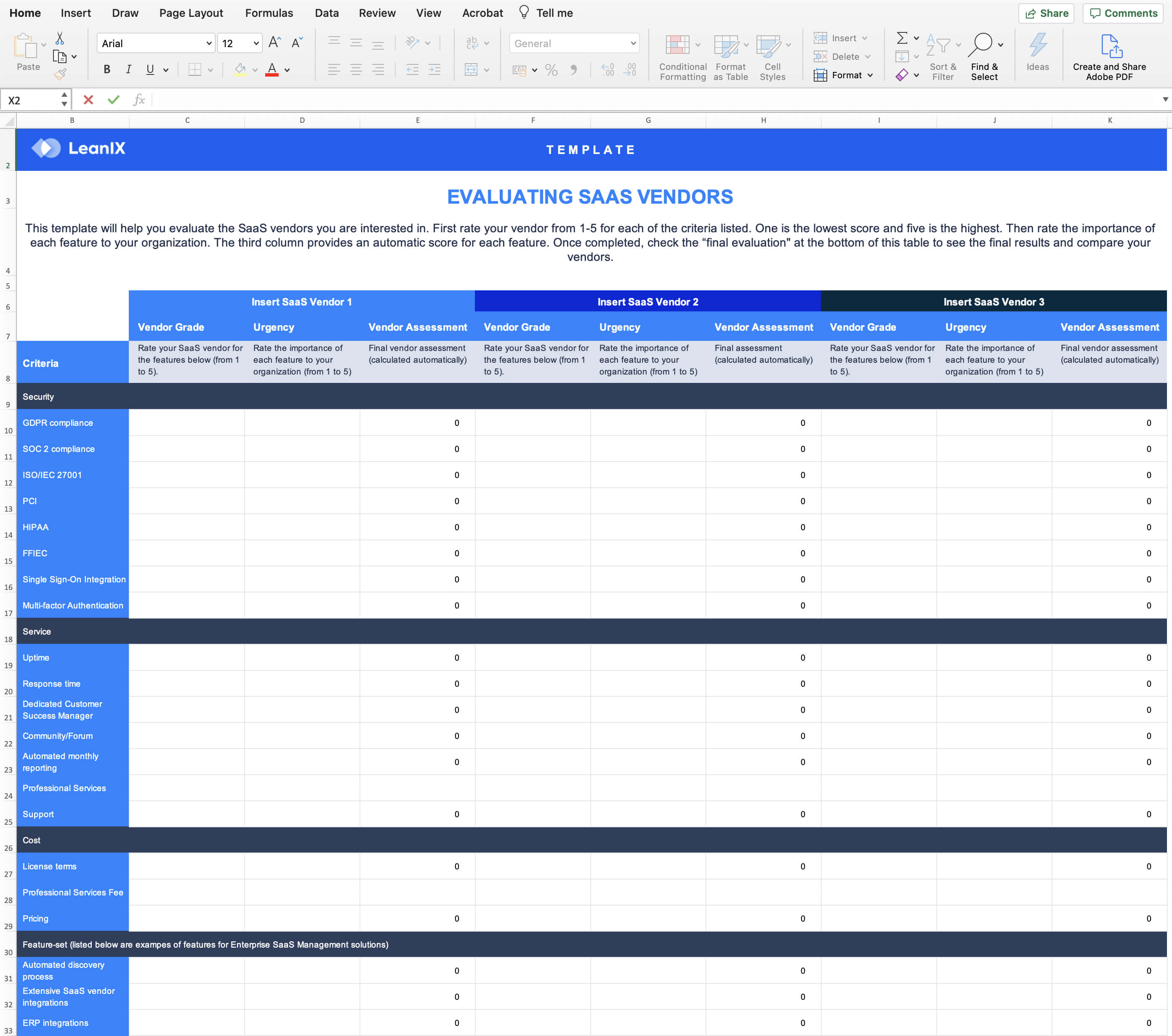
SaaS security checklist
A SaaS security checklist is necessary when a company is evaluating the security of a new SaaS solution, and procurement should not move forward unless a proper SaaS risk assessment has been conducted and received the approval of the internal security teams.
It is a separate process to a technology risk assessment that evaluates application risks, reduces costs, and increases agility. A SaaS security application checklist is created and completed by the external supplier before moving forward with a company. An important part of this process is ensuring end-to-end encryption is in place, which guarantees data will not be shared with third parties or can be accessed by the provider.
General information
The first part of the SaaS security questionnaire will contain general information about the vendor before moving into more detailed questions regarding the security of the vendor. General information includes the contact details as well as how long the vendor has been in business. Here is the full list of questions in the general information section of the SaaS security checklist:
- Date completed
- Vendor name
- Service(s) / Product(s) provided
- How long has the vendor been in business?
- What year was the vendor founded?
- Supplier location(s) and headquarters
- Supplier website domain(s)
- Completed by
- Title
- Email
- Telephone
Information security
This section and the subsections within go much more into detail regarding the security information of the product. Each subsection of the SaaS security checklist will assess whether the product is fit for its purpose and in line with your company’s security protocols.
Organizational security
This subsection of the SaaS security checklist outlines who is responsible for information security and what policies have already been implemented to ensure the security of the data between the company and the supplier. The questions are as follows:
- Does the supplier have a designated leader responsible for information security?
- What is the name of the Information Security leader? Title? Role?
- Policy for information security implemented
HR security
Much like organizational security, human resources security covers who the company will be working with and what kind of access they have to sensitive information. This part of the SaaS security questionnaire asks whether the vendor has sufficient onboarding and offboarding processes, if they perform background checks and whether they receive security training.
- Have all personnel with access to your company information signed the Non-Disclosure Agreement (NDA) of the Supplier?
- Is there a personnel onboarding and offboarding process?
- Does the supplier perform background verification checks for all its personnel?
- Is regular security training for all personnel implemented? Please confirm whether these are imparted at the time of onboarding and if a refresher is conducted annually.
Physical site
This part of the SaaS security questionnaire will outline where on the physical site the servers will be kept, and what kind of physical security is in place to protect sensitive company data.
- Please state the locations of data centers/server rooms
- Location where the backups are stored
- Do you have a physical and environmental security policy that covers both data center and vendor premises?
Application and network security
During this subsection of the SaaS security checklist, the company is asking whether the applications and network are regularly tested for security breaches, and what kinds of countermeasures are in place to stop that from happening.
- Do you perform application and network-level penetration tests?
- Please share countermeasures for network risks (e.g. firewall, HIDS, etc.)
- Are there password selection and management controls in place for accessing your company information?
- Are there Identity and Access management (IAM) controls in place for access to your company information?
Asset management
How are the assets managed within the company, and how are each of the supplier’s clients’ data and information stored to ensure it is kept separate from each other? This part of the questionnaire will also require the vendor to outline a risk management methodology.
- Is there a policy in place to handle your company information as confidential?
- Is your company information processed and stored logically separated from suppliers’ information and from that of other customers?
- Do you have a risk assessment/risk management methodology?
- Upon conclusion or termination of vendor's work for your company, will supplier sanitize and securely destroy (or at your company's election return to your company) all copies of all your company information, including all backup and archival copies, in any electronic or non-electronic form?
System acquisition, development, and maintenance
This subsection of the SaaS security questionnaire will cover how the applications mitigate risk, and what processes are in place for development, testing, and operations. The vendor is required to share software development methodology and what security measures are incorporated as part of the application development life cycle.
- Are development, testing, and operational environments containing your company information separated from each other?
- Does the application offered to your company mitigate risks as specified in OWASP Top 10 2017 list?
Sub-contractor relationships
What does the relationship between the vendor and third-party subcontractors look like? This is important to outline who the subcontractors are, and what processes they use. This part of the SaaS security checklist should list all subcontractors.
- Will the vendor use any Third Party Sub-Processors? If Yes, Which ones?
Incident management
Incidents can always happen, so this section of the SaaS security questionnaire will require information on what incidents have occurred in the last year, and what incident management processes are already in place. The vendor must share their incident management policy.
- Is there a documented security incident management process in place to detect and handle incidents?
- Have you had any material events or incidents on the service provision in the last 12 months? Please provide the information on the response times.



/EN-WP-IT_Cost_Savings-Resource_Page_Thumbnail.png?width=260&height=171&name=EN-WP-IT_Cost_Savings-Resource_Page_Thumbnail.png)
/EN-WP-EA-Tomorrow-Resource_Page_Thumbnail.png?width=260&height=171&name=EN-WP-EA-Tomorrow-Resource_Page_Thumbnail.png)