
On May 25th, 2018, the European Union’s General Data Protection Regulation (GDPR), designed to reform data protection in Europe comes into force worldwide. This particular regulation is the result of over 4 years of collaboration between the European Council & Parliament, who desired to make a more clarified stance on the protection of citizens’ personal data. The GDPR includes directives to protect citizens’ fundamental rights, gives data subjects a wider range of rights, and specifically includes the personal data of victims, witnesses, and suspects of crime.
The GDPR brings with it massive penalties for noncompliance, yet American research and advisory firm Gartner predicts that over half of all businesses are not prepared for the legislation. In this post, we will explain the history of data protection in Europe, fast facts about what changes under GDPR for companies around the world, the proposed penalties, and how organizations can use Enterprise Architecture to prepare for the regulation.
History of Data Protection in Europe:
There's no question - The European Commission cares about the protection of their citizens’ data. From early 2012 until now, the European Commission, the Council, and the Parliament have continually met to update laws and regulations regarding the data protection of its citizens.
European Data Protection Timeline:
- 25 January 2012, the European Commission proposed a comprehensive reform of data protection rules to increase users' control of their data and to cut costs for businesses.
- 13 May 2014, the Court of Justice of the European Union acknowledged that under existing European data protection legislation, EU citizens have the right to request internet search engines to remove search results directly related to them. This sparked a lively debate on the “right to be forgotten.”
- 15 December 2015 - the European Parliament, the Commission, and the Council reach an agreement on the GDPR.
- 6 May 2015 The Digital Single Market Strategy was officially announced. The strategy was made up of three pillars -
- Access to online products and services
- Conditions for digital networks and services to grow and thrive
- Growth of the European digital economy
The Digital Single Market Strategy did away with the expensive EU roaming charges and valued the European trade markets as the highest in the world for online businesses. Today, the EU online spend is valued at just under €500 billion, a figure expected to double by 2020. According to the Juncker Commission, a fully functional Digital Single Market could contribute €415 billion per year to the EU economy.
- 8 April 2016, the European Council adopted the GDPR regulation.
- 14 April 2016, the Regulation and the Directive were adopted by the European Parliament.
- 4 May 2016, the official texts of the Regulation and the Directive were published in the EU Official Journal in all the official languages.
- 25 May 2016, the GDPR regulation applies from this date.
- 6 May 2018, all EU Member States have two years to transpose it into their national law, and it will be enforced globally.
Key Changes Under GDPR
The GDPR introduces many new data accountability obligations, data restrictions, and security parameters that every business in the world that processes European citizens’ information must comply with.
Increased Territorial Scope
Arguably the biggest change to the regulatory landscape of data privacy comes with the extended jurisdiction of the GDPR, as it applies to all companies processing the personal data of data subjects residing in the Union, regardless of the company’s location.
Penalties
The fine schedule is as follows:
- €10 million or 2% of the global revenue of the prior year
If it is determined that noncompliance was related to technical measures:
Examples that fall into this category are:
- Not having records in order
- Failing to conduct impact assessments
- Failing to notify the supervising authority and data subject about a breach in a timely manner
- €20 million or 4% of the global revenue of the prior year
Applied to cases of noncompliance with key provisions of the GDPR.
Examples that fall into this category are:
- Non-adherence to the core principles of processing personal data
- Infringement of the rights of data subjects
- Transferring of personal data to third countries
- Failing to ensure an adequate level of data protection
*It is important to note that these rules apply to both controllers and processors, which means that 'clouds' will not be exempt from GDPR enforcement.
In Comparison: Security fines before and after GDPR
As a comparison, here are two cases of fines sanctioned by the Information Commissioner's Office (ICO) upon companies that failed to protect the data of their customers:
TalkTalk's 2016 fine of €435,000 for security failings that allowed hackers to access customer data would rocket to €64m under GDPR in 2018. Pharmacy2U's fine of €140,000 would balloon to €47.8m under GDPR.
Fines levied under GDPR could be considerable enough to permanently close down operations. It will be much cheaper to prepare your company of the impending regulation than it would be to pay millions of fines for each offense.
Consent
The conditions for consent have been strengthened. Companies will no longer be able to use 25-page terms and conditions documents full of difficult jargon and legalese. The request for consent must be given in an easily accessible form, with the purpose of data processing attached to that consent. Consent must be clear and distinguishable from other matters and provided in an intelligible and easily accessible form, using clear and plain language. It must be as easy to withdraw consent as it is to give it.
DATA SUBJECT RIGHTS
Breach Notification
Under the GDPR, breach notification will become mandatory in all member states where a data breach is likely to “result in a risk for the rights and freedoms of individuals”. This must be done within 72 hours of first having become aware of the breach. Data processors will also be required to notify their customers, the controllers, “without undue delay” after first becoming aware of a data breach.
Right to Access
The right for data subjects to question the data controller as to whether or not personal data concerning them is being processed, where and for what purpose. Further, the controller shall provide a copy of the personal data, free of charge, in an electronic format. This change is a dramatic shift to data transparency and empowerment of data subjects.
Right to be Forgotten
Also known as Data Erasure, the right to be forgotten entitles the data subject to have the data controller erase his/her personal data, cease further dissemination of the data, and potentially have third parties halt processing of the data. Conditions for erasure include the data no longer being relevant to original purposes for processing, or a data subject withdrawing consent.
Data Portability
The right for a data subject to receive the personal data concerning them, which they have previously provided in a 'commonly used and machine readable format' and have the right to transmit that data to another controller.
Privacy by Design
Privacy by design calls for the inclusion of data protection from the onset of the designing of systems, rather than an addition. Article 23 calls for controllers to hold and process only the data absolutely necessary for the completion of its duties (data minimization), as well as limiting the access to personal data to those needing to act out the processing.
Data Protection Officers
Your organization is required to appoint a Data Protection Officer (DPO) for your business if the core activities of your company consist of personal data processing which
- requires regular and systematic monitoring of individuals on a large scale; or
- is about special categories of data on a large scale and data relating to criminal convictions and offenses. ‘Special categories of data’ is the type of data that reveals the racial or ethnic origin, political opinions, religious or philosophical beliefs, trade-union membership; genetic data, biometric data, or data concerning health or sex life, and sexual orientation.
*Please note that even if none of the situations apply to your processing, and even if you are not established in the EU but only processing data of individuals who are in the EU, you may still have to appoint a DPO if it is required by the Member State law where your processing relates to.
Importantly, the DPO:
- Must be appointed on the basis of professional qualities and, in particular, expert knowledge of data protection law and practices.
- May be a staff member or an external service provider.
- Contact details must be provided to the relevant DPA.
- Must be provided with appropriate resources to carry out their tasks and maintain their expert knowledge.
- Must report directly to the highest level of management.
- Must not carry out any other tasks that could result in a conflict of interest.
Is your company required to appoint a DPO under the EU GDPR? LeanIX has created a simple decision tree that plainly illustrates if your company will be required to hire a DPO.
What GDPR means for businesses outside of Europe -
Contrary to what the name suggests, the GDPR does not only affect European businesses but any firm that collects the data of European citizens including European e-commerce clients and companies with satellite offices staffed with European employees.
As the European Union stands out for its comprehensive approach, organizations in non-European countries don't have the same historical experience with approaching sensitive data.
GDPR focuses on Personally Identifiable Information (PII) which is defined as any information that can be used on its own or with other information to identify, contact, or locate a single person, or to identify an individual in context. PII can be sensitive or nonsensitive. PII includes biometric information (e.g. gender, birth date, etc), medical information, personally identifiable financial information, and other sensitive identifiers such as driver's license information, passport, or Social Security numbers. This information is routinely collected throughout normal e-commerce transactions, customer correspondence, and website analytics.
Major changes for non-European businesses -
The GDPR brings organizational changes, stricter application management, and increased transparency for the storage and management of data. Just understanding where data is stored, how to quickly access it, and modify data based on the needs and concerns of the customer is a simple directive that can be tricky to streamline for a US business that operates globally.
- DATA PROTECTION THROUGH TECHNOLOGY (ART. 25 GDPR)
Companies are required to define internal strategies and initiate steps to ensure data protection through technology (by design) and as a standard approach (by default). Possible measures include minimizing and pseudonymizing the processing of personal data.
- ACCOUNTABILITY (ART. 5 GDPR)
Companies are required to ensure and demonstrate adherence to data protection regulations, for example through certification.
- NOTIFICATION REQUIREMENTS (ART. 33 GDPR)
Companies are required to report data breaches (e.g. through hacking attacks) immediately, within 72 hours, to the competent supervisory authority and the affected data subjects. Failure to do so may lead to fines of up to 20 million euros or 4% of the company's global annual turnover.
- ENHANCED RIGHTS FOR INDIVIDUALS (ART. 17 GDPR)
These include the right to be forgotten, the right to request the porting of one’s personal data to a new organization, the right to object to certain processing activities, and the right for certain data to be deleted.
Enterprise Architects and GDPR
Successfully preparing your business for integrating the GDPR will require a great deal of architectural work. A study found that companies consider ensuring data quality (73%) and handling data complexity (67%) to be the greatest obstacles to GDPR compliance.
The Enterprise Architect of your team can provide access to this information. EAs act as an interface to numerous stakeholders and can answer almost any question that contributes to GDPR compliance. The basic prerequisite here is that work on the Enterprise Architecture has been well implemented, architectural best practices are applied and modern tools are used.
Of course, EAs cannot cover all the requirements of the GDPR; close cooperation between the key managers is therefore indispensable. An initial overview of the various data protection criteria and the interfaces to key managers can be found in the LeanIX GDPR Requirements Catalog. It will also show you where and how an EA tool can help you with GDPR implementation and when it is advisable to consult the data protection officer and the technology owners.
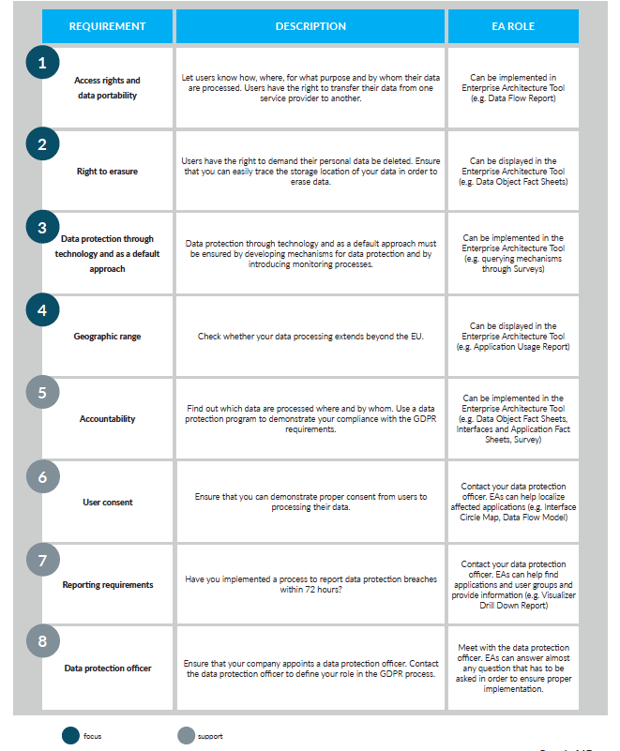
Figure 2: GDPR Requirements Catalog
GDPR COMPLIANCE IN FIVE PRACTICAL STEPS WITH EA
1. Contact GDPR Stakeholders
Contact other GDPR stakeholders to coordinate your next steps: in many organizations, EAs do not have final responsibility for compliance with legal regulations. This responsibility may lie with your legal department, the chief risk officer, the chief compliance officer, the chief information security officer, or the data protection officer. Designate and contact these people in order to coordinate your actions.
2. Identify Personal Data
Creating a data inventory is crucial to meeting the requirements of the GDPR documentation. The key to GDPR compliance is having a clear overview of your data - how your company processes it, where it is stored, and how to quickly access it to make key changes. Collecting this information can be a daunting and time-consuming task, and you may not have all of the information that you need.
LeanIX Survey gives you the tools to answer many key GDPR compliance questions, such as: "Who is responsible for the processing of personal data? Which applications use these data?Are they additionally processed and stored outside the EU?" Addressed to the responsible GDPR stakeholders, the stakeholders can fill out a questionnaire and provide you with the required information through the Survey. Use the "Subscriptions" section in LeanIX (see fig. 3) to identify the responsibilities of individual stakeholders with regard to a specific object. 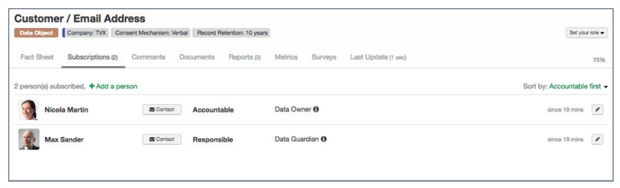
Figure 3 - Identifying responsibilities and ownership of data objects in LeanIX
Subscriptions can also be used in the Filter and the Survey add-on, so you can filter e.g. for all data objects for which a certain user is the data owner. Identify all data that is defined as personal data according to the GDPR. Essentially, any information relating to customer master data and employee data is personal data. Pay particular attention to sensitive data; as the GDPR prohibits their use. Then assess the data to determine their level of privacy sensitivity, categorizing them as public/unclassified, sensitive, restricted, or confidential. You can use LeanIX tags to add further attributes (e.g. "GDPR restricted") to a data object or application. This will usually already be part of your internal security processes, where you assign attributes such as confidentiality, integrity or availability to data.
3. Detect and Assess Risks
Around 76% of German businesses state that due to the complexity of modern IT services, they do not always know where their customer data is located. Imagine a consumer who wants to make use of her "right to be forgotten". In order to delete her data, you have to know where the data is stored. An EA tool like LeanIX allows you to effectively implement these processes.
LeanIX's Data Flow Model (see fig, 4) is an automated visualization that shows which data objects are used by which applications and which business capabilities in turn depend on them. The data flow is generated automatically and can be expanded by adding details such as the IT components and user groups of certain applications. Labels next to the interfaces display their attributes, such as interface technology, data objects, and frequency.
Then assess your application landscape for risk. The level of risk can be determined through a range of different parameters, in particular however with regard to the business impact, application dependencies, critical levels, failure scenarios, and previous incidents.
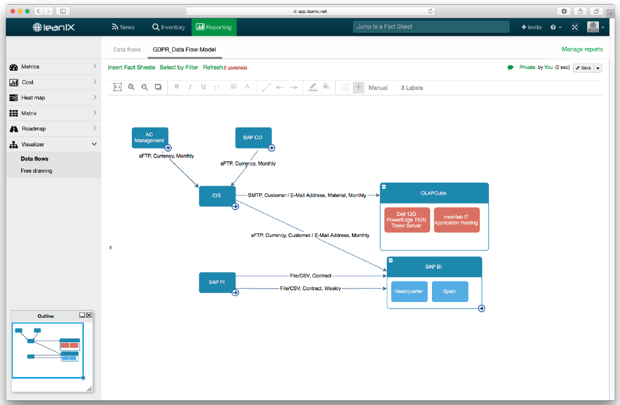
Figure 4 - Data Flow Model in LeanIX
Visualizations such as the Data Flow Model (see fig. 4) and the Heat Map (see figure 5.) provide information on business-critical consequences for your company in the event of an application failure or hacking attack (see fig. 6). Risk Dependency Maps and Interface Circle Maps visualize the various dependencies between multiple applications. The more dependencies an application has, the higher the level of risk in the event of a failure (see fig. 8–9). You can additionally use a Survey when querying information on possible failure scenarios and incidents in the past in order to assess the risk level.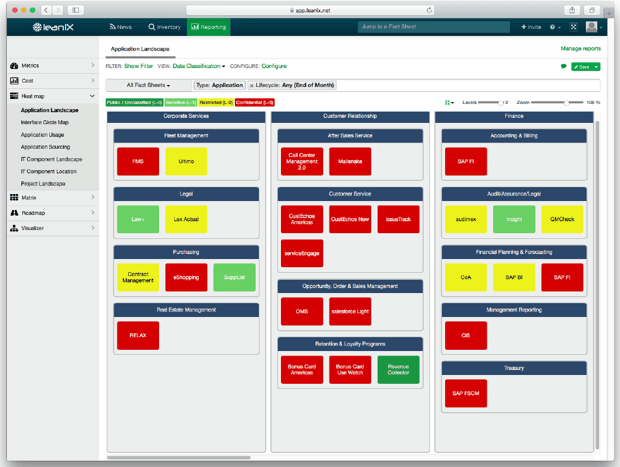
Figure 5 - Heat Map of business impact in LeanIX
Visualizations such as the above-described Heat Map (see fig. 5) can provide information on business-critical consequences for your company in the event of an application failure or hacking attack (see fig. 6).
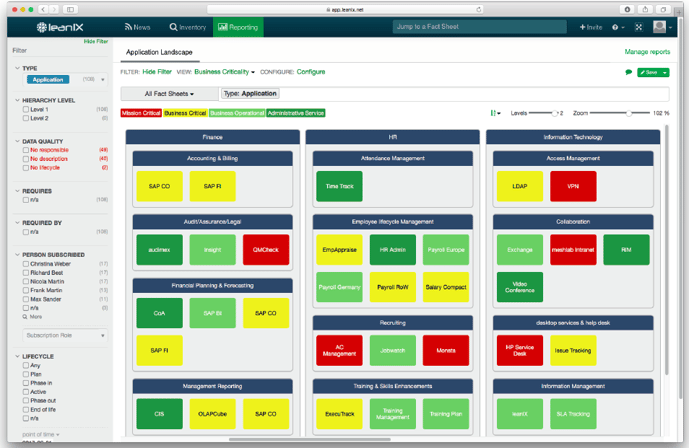
Figure 6: Heat Map of business impact in LeanIX displaying business-critical consequences in the event of an application failure or hacking attack
Risk Dependency Maps (see fig. 7) and Interface Circle Maps (see fig. 8) visualize the various dependencies between multiple applications. The more dependencies an application has, the higher the level of risk in the event of a failure.
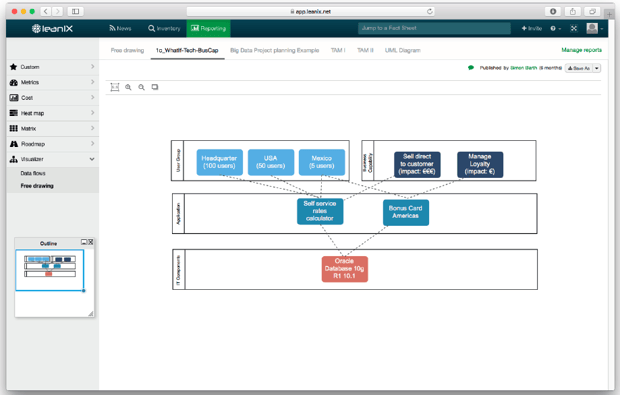
Figure 7: Risk Dependency Map
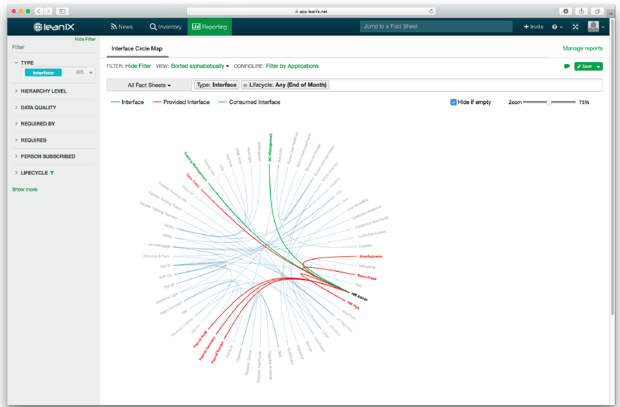
Figure 8: Identifying dependencies with the Interface Circle Map in LeanIX
You can additionally use a Risk Assessment Survey when querying information on possible failure scenarios and incidents in the past in order to assess the risk level.
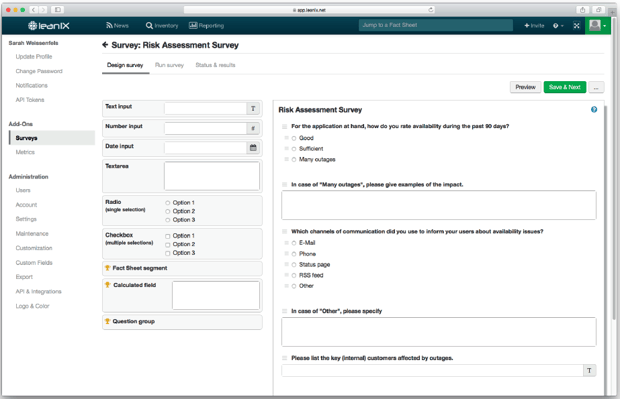
Figure 9: Risk Assessment Survey in LeanIX dashboard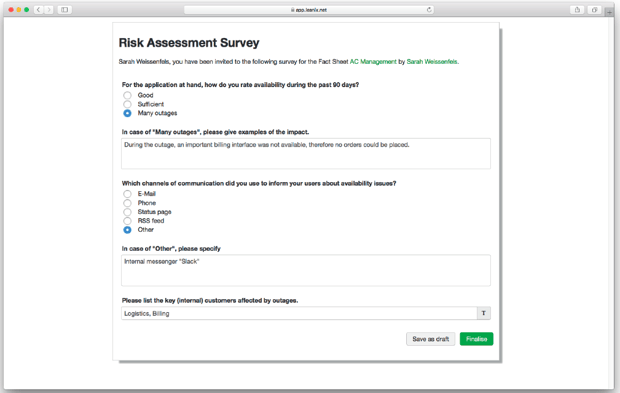
Figure 10: Risk Assessment Survey in LeanIX continued.
We recommend starting with areas that have a high-risk factor and process sensitive data. Answer questions such as: Where could potential vulnerabilities in the business and IT landscape lie? What are frequent threats that could exploit these vulnerabilities? What are the possible consequences?
For example, think of an application that is deeply embedded in the IT landscape via multiple interfaces. If it fails, the effects can be severe. Imagine a CRM system that plays a major role in customer data and has interfaces to Microsoft Exchange, mailing tools, help desk tools, content management systems, and much more. Its high level of connectivity means the potential effects on other applications and processes are multiplied. Heat Maps, Interface Circle Maps, and Risk Dependency Maps help you gain an overview of your company's risk portfolio and thus serve important decision-makers as the first basis for risk management and control.
4. Define checks and implement measures
Once you have correctly assessed the technology risks, you need to implement concrete security checks and preventative measures. The IT security checks in ISO 27001 can serve as a guideline here. Introduce important measures as soon as possible in order to implement the data protection by technology approach (e.g. pseudonymizing personal data); this will save you time and money when upgrading. Always ask yourself:
- How well does your application portfolio meet security standards?
- How are your security standards developing over time?
The LeanIX Survey feature provides the initial answers as a starting point for defining useful security checks and appropriate measures. Imagine a content management system that collects customer data that in turn is transferred to mailing tools and CRM systems via a range of interfaces. A survey allows you to query and identify deficits in your IT landscape, e.g. if your company currently has no demonstrable consent from the addressees because the application owner has not implemented a double opt-in process. The responsible owner can provide possible recommendations for preventative measures via the comment field in the Survey feature.
Further vulnerabilities, such as the recording of nonrelevant or duplicate data, can also be queried via Survey. If your company is for example collecting entrant data for an online competition (e.g. name, address, and date of birth), only the first two items are required to determine the winner, whereas the date of birth is not.
Therefore, you must point out that submitting these data is voluntary and indicate why you are requesting them (rule of data minimization). LeanIX will help you uncover vulnerabilities and systematically follow up on their correction. Then transfer the measures you have defined in your organization, your processes, and systems into projects. The previously described Survey can be used repeatedly over a longer period of time to monitor the checking process and document the development of measures. Comparing the results will assist you in the GDPR implementation process.
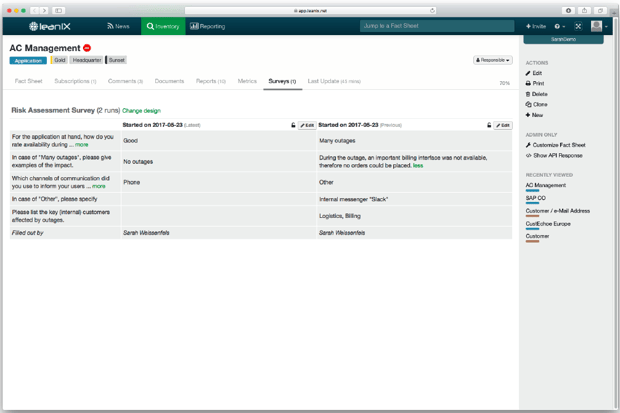
Figure 11: Survey query over a specific period in LeanIX
5. Demonstrate GDPR Compliance
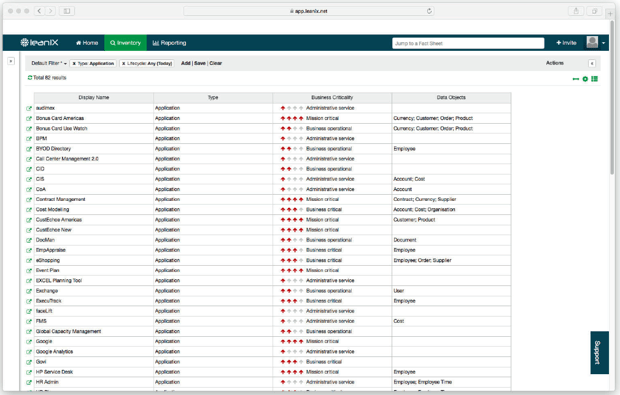
Demonstrate your compliance with GDPR guidelines by showing how you process personal data, how you handle risks, and what measures for damage limitation you have implemented. The latter is especially relevant when you conduct a DPIA, which the GDPR requires for every implementation of a new system that uses personal data. Use the LeanIX Inventory View function (see fig. 12) and present your GDPR compliance by providing a quick and clear overview in table form of all applications, interfaces, data objects, and technologies.
Regularly reviewing GDPR compliance and demonstrating data currency is easy if you have a current data basis on your IT landscape. LeanIX helps you achieve this transparency and offers many ways of ensuring that your data are always up to date. You can for example access your Surveys, where you have documented the entire progress of your GDPR implementation. Data quality workflows help responsible managers ensure their data are up to date at regular intervals. And the collaborative elements of LeanIX enable all GDPR stakeholders to easily work together on a single platform.
Get prepared for GDPR.
Just in the past 4 years, the EU has enacted many laws and regulations to protect consumer data. This means a lot of changes for IT-specific companies, including timely breach notification, the right data to access, the right to be forgotten, and privacy by design. Complying with GDPR will bring major changes to your IT landscape, or your company may be subjected to hefty fines.
To learn the best practices in preparing for GDPR compliance, schedule a DEMO with one of our dedicated team members.






